SarCTF
On February 15-16, 2020, the online CTF (jeopardy) competition was held - SarCTF, with the support of the Saratov State University.
鹅国某个大学主办的CTF,由于有时差,比赛15号晚上十点才开始,持续24小时。logo设计的不错,第一眼看上去,还以为右上角是只熊,仔细一看,原来是个帽子…不得不吐嘈一下主办方的服务器,十点一到,瞬间挤爆,各种连接不上,主办方折腾了半天,推迟到十点半,比赛终于开始了。
刷新了许久,终于刷出Challenges的我直接奔向逆向题,扫了一眼,一共有三道题,一道linux,两道win,由于担心服务器不一会儿后又会宕掉,于是就全下载了下来。
linux那题极为简单,1分钟就做完了,没成想,提交flag却卡了整整5分钟…交完flag的我,正准备解决剩下两道题,随手刷新了一下页面,嗯??逆向的题消失了,只剩下我刚做的一道了…莫非是题目出问题了?于是看了看群里的消息,有个师傅吐嘈道:
Yeah I went to input flag and it’s gone haha
翻译:我刚想交flag,题目就消失了,哈哈(尬笑)。
主办方如是回答道:
These two jobs will not be deleted and will not be returned.
翻译:这两道题没有被删除,但是你也别想再看到他们了。
嗯??这是什么神仙操作……
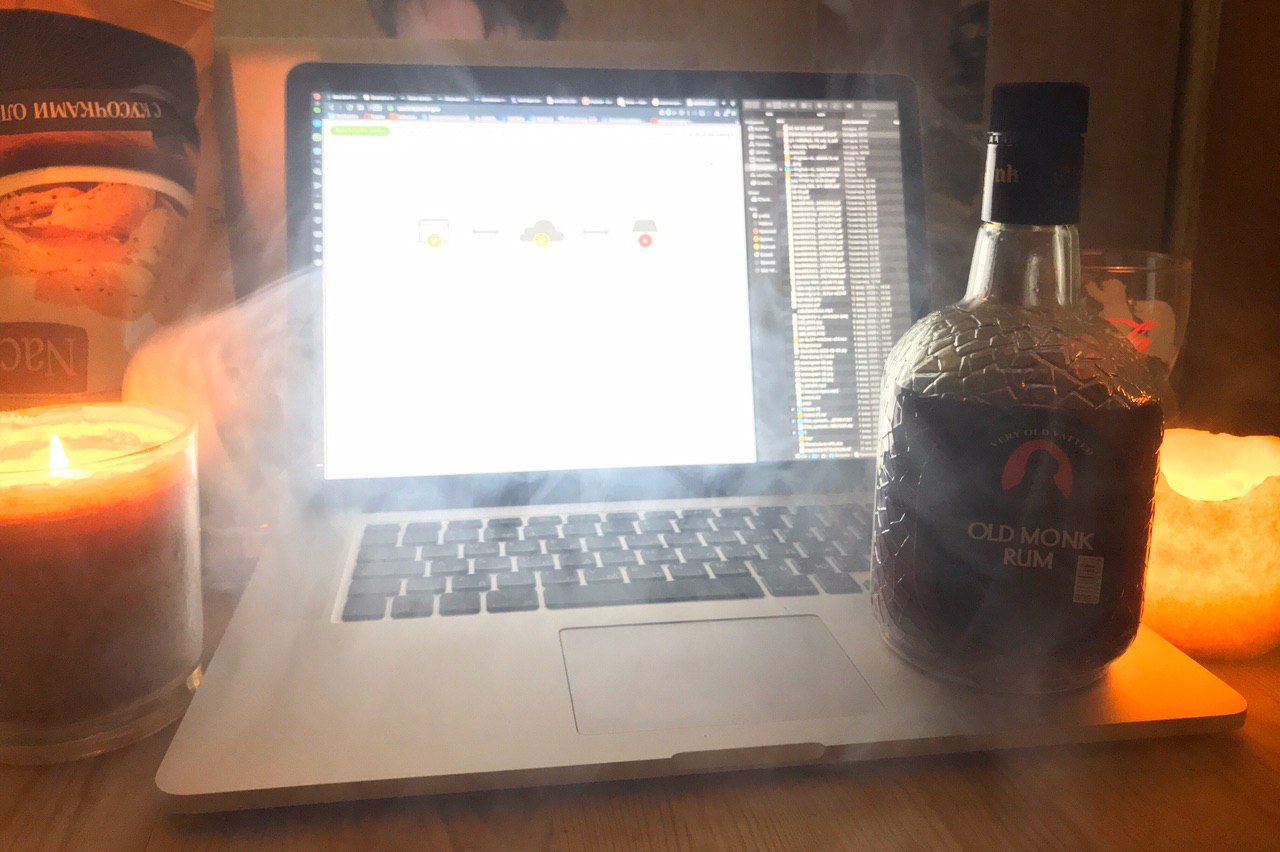
说到官方交流群,倒是有不少好玩儿的,其中有位俄国老兄,发了张图片:
一台电脑,一壶烈酒,点点灯光,此情此景,虽不乏惬意,却也是十分壮烈,不愧是战斗民族…
p.s.此时电脑屏幕显示的是502Error(网关挂掉了)
好了,闲言少叙,回归正题,这次比赛是跟学校里的另外六名小伙伴儿组队参加的(我第一次组队参加线上赛!终于不是孤身一人了哈哈)虽说解出的题目不多,但也涨了不少见识。刚开赛的时候排名还比较靠前,大概在十几名,后来大家都困了就都去睡觉了,第二天一起来,排名就掉到了100开外,于是一路猛追,最终在417个队伍里面排名第47,也还不错啦~


这次比赛的题型居然没有pwn,不过多了个PPC(Professional Programming Challenges),看着比较新鲜,其实就是考察编程能力,其实也没有考察什么编程能力,顶多算是处理socket的输入输出…
Reverse
Crossw0rd
题目描述:
While the children were playing toys, Sherlock was solving crosswords in large volumes.
考察点:逆向分析
难度:入门
初始分值:1000
最终分值:309
完成人数:264
非常简单的逆向分析题,首先反汇编程序,分析程序流程:
1 | unsigned __int64 check(void){ |
流程很简单,就是检查输入的字符串是否为flag,检查字符串的有6个函数,分别如下:
1 | _BOOL8 __fastcall e(char *a1){ |
1 | _BOOL8 __fastcall b(char *a1){ |
1 | _BOOL8 __fastcall d(char *a1){ |
剩下的三个函数都差不多,就不一一列出了,其中a1就是我们输入的字符串,这些函数做的就是检查字符串中的某个字节是否正确。
解法很简单,只要在相应位置填入对应的字符,即可拼得flag(不用写脚本,打个草稿就行):
FLAG{3a5yr3v3r5ing}
PPC
Mind palace I
题目描述:
It looks like the situation is hopeless, there is no time to think. However, you can use the mind palace and solve all problems instantly.
Code1
nc 212.47.229.1 33001
考察点:摩尔斯电码、socket编程
难度:简单
初始分值:1000
最终分值:802
完成人数:142
nc连接上题目,显示有一个字符串pip,过了一会儿变成了piiiip,过了一会又变回去了,就这样一直跳来跳去……刚开始没意识到,后来经过imagin师傅提醒,可能是摩尔斯电码,于是dump出数据,将pip视作.(dot),将piiiip视作-(dash),得到摩尔斯电码:
…. . .-. . ..- .–. — -. - …. . .-.. .- .–. . .-.. — ..-. – -.– -.-. — .- - -.– — ..- – .- -.– … . . - …. . .-. .. -… -… — -. — ..-. – -.– -.. . -.-. — .-. .- - .. — -. -… ..- - - …. . – . -.. .- .-.. .. - … . .-.. ..-. .. -.- . . .–. .. -. .- .-.. . .- - …. . .-. -. .–. — ..- -.-. …. .- - …. — – . ..-. .-.. .- –. … …. . .-. .-.. — -.-. -.- .-.. .. -.- . … -.– — ..- .-. – — .-. … .
解密后得到字符串:
HERE UPON THE LAPEL OF MY COAT YOU MAY SEE THE RIBBON OF MY DECORATION BUT THE MEDAL ITSELF I KEEP IN A LEATHERN POUCH AT HOME FLAG SHERLOCK LIKES YOUR MORSE
刚开始直接扔到google翻译里,愣是没找到Flag在哪儿,后来仔细看了下,倒数5个单词开始就是FLAG
FLAG{SHERLOCK_LIKES_YOUR_MORSE}
dump数据的脚本如下:
1 | #!/usr/bin/python |
Mind palace II
题目描述:
It’s time to strain your brains.
Code1
nc 212.47.229.1 33002
考察点:ROT13、socket编程
难度:简单
初始分值:1000
最终分值:890
完成人数:106
nc连接上题目后,显示如下内容,分析下不难看出message为密文,将其rot13解密之后的结果输入answer中,就会出现下一个密文
1 | nc 212.47.229.1 33002 |
解密100轮之后就会给flag,脚本如下:
1 | #!/usr/bin/python |
Mind palace III
题目描述:
100% of brain CPU
Code1
nc 212.47.229.1 33003
考察点:逻辑运算、socket编程
难度:简单
初始分值:1000
最终分值:896
完成人数:103
nc连接上题目后,显示如下内容,分析下不难看出是要输入逻辑运算后的结果,结果正确就会出现下一个运算式:
1 | nc 212.47.229.1 33003 |
算对100次之后就会给flag,脚本如下:
1 | #!/usr/bin/python |
Misc
Deep dive
题目给了附件flag.txt,用file指令识别下,发现它实际上是个压缩包
1 | file flag.txt |
经过解压后还是个压缩包,但是换了一种压缩方式:
1 | tar xvf flag.txt |
至此大概明白这题要考察的就是自动解压缩包,不同压缩类型的压缩包需要不同的指令来解压,所以此题关键在于正确识别文件类型。python有个filetype库可以实现文件类型识别。
根据压缩包类型解压,大概解压700多次就有flag了(膜Y1ng师傅手动解压300余次)脚本如下:
1 | #!/usr/bin/python |
True Detective
题目描述:
And now it’s time to show the skills of a real detective!
考察点:信息搜索、源码分析
难度:简单
初始分值:2000
最终分值:1681
完成人数:124
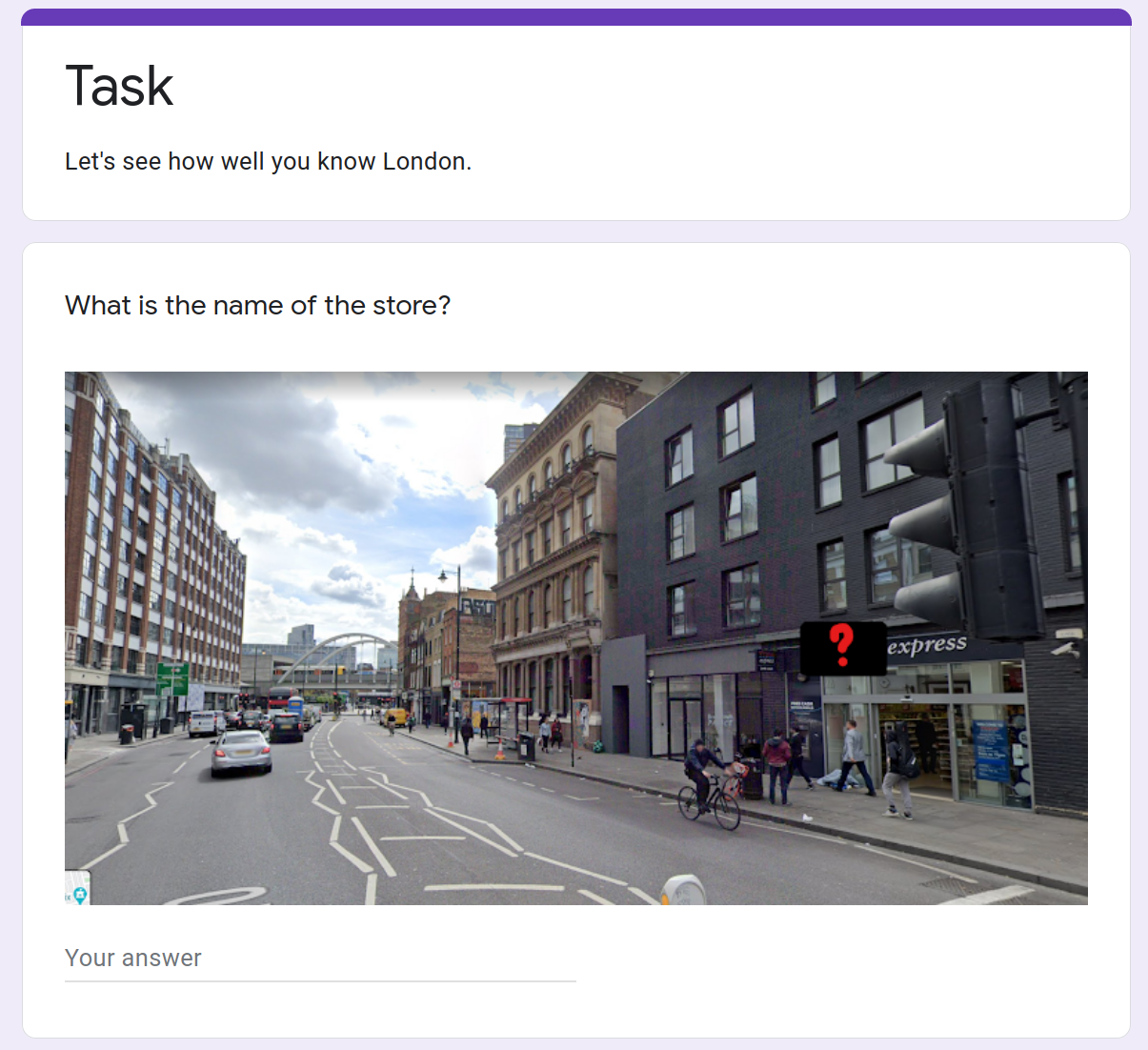
题目描述给的链接是个google文档,打开之后这样:
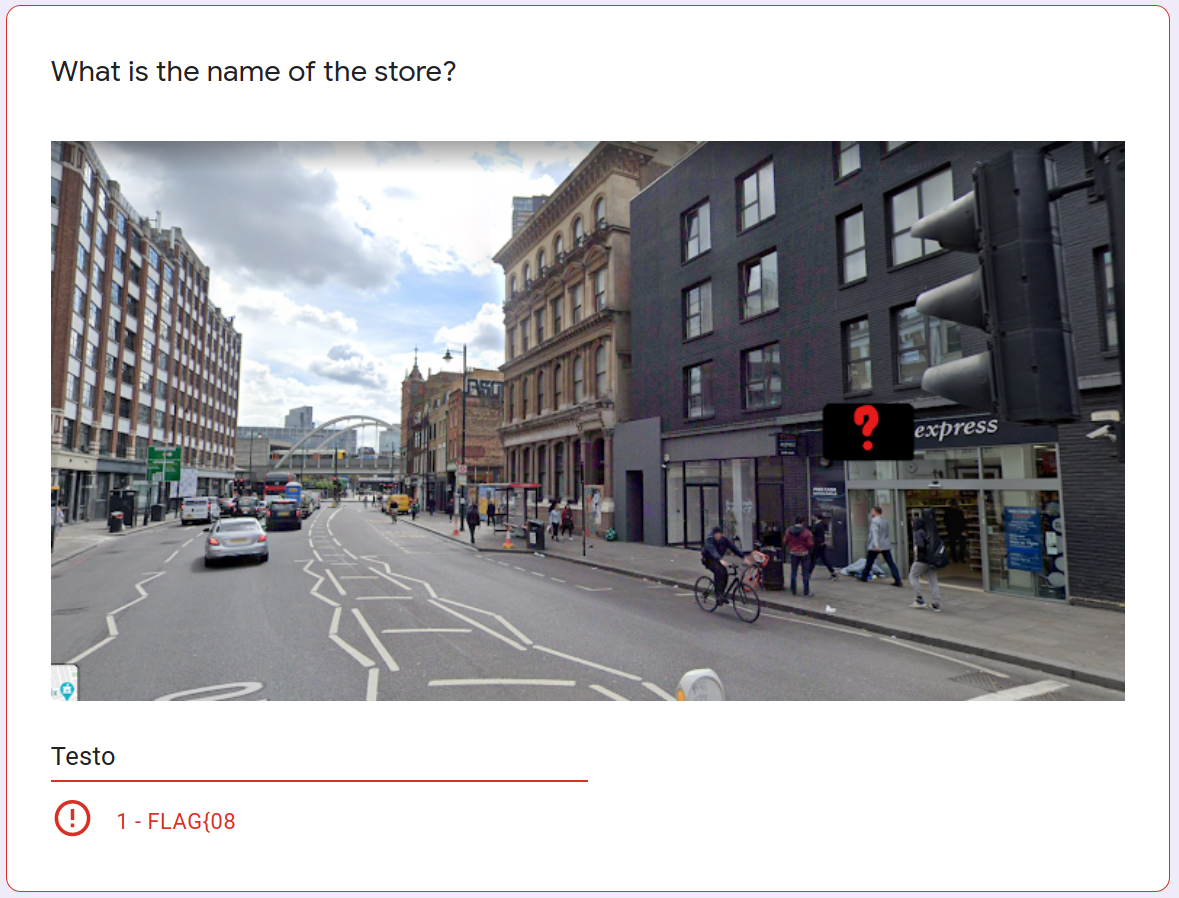
要求回答5个关于伦敦的问题,天真的我以为这题是要考搜索能力,于是google了这个图片(图片店名被挡住了),发现这家店全名叫做Testo,输入Testo给了flag的第一部分
后来越往后做越难,什么根据图片找出地名、图片中的是哪国大使馆、这是什么公园之类的…这谁知道呀
于是审查了一下网页元素,搜索FLAG{08发现flag其实就在源码中……而且是通过js判断答案的:
1 | var FB_PUBLIC_LOAD_DATA_ = [null,["Let's see how well you know London.", |
flag有5部分,拼全就是答案:
1 - FLAG{08
2 - c49c3d9a
3 - e8898343
4 - 7729747b
5 - cf1be8}FLAG{08c49c3d9ae88983437729747bcf1be8}
end
国际小比赛,题型和国内CTF有所不同,挺好玩儿的,以后有时间还玩儿~